The Internet Iceberg Analogy
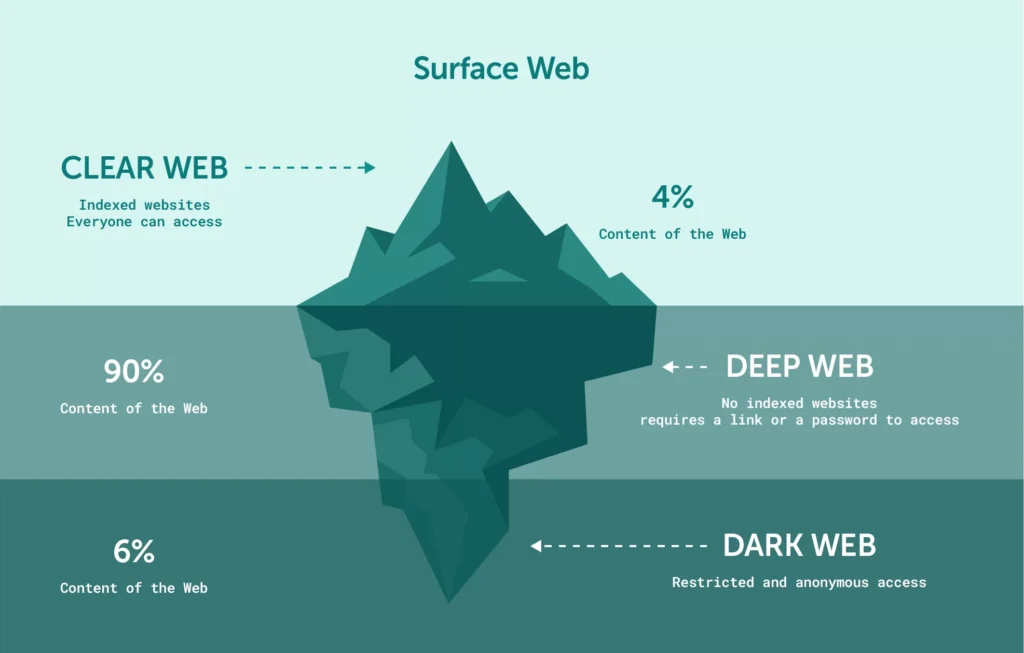
The internet we interact with daily—platforms like Google, Facebook, or YouTube—represents merely the tip of a vast digital iceberg, known as the Surface Web. It is estimated that this visible portion accounts for only about 4% to 10% of the total information available on the internet.
The remaining 90% or more lies submerged beneath the surface—this is the Deep Web. Within this massive, hidden domain lies the deepest, most dangerous, and intentionally concealed section: the Dark Web.
The terms “Deep Web” and “Dark Web” are frequently, yet incorrectly, used interchangeably. The distinction between them is crucial for understanding modern cybersecurity threats.
This analytical guide aims to thoroughly dissect the structure of this hidden world, clarify the fundamental differences between the Deep Web and the Dark Web, explain the operational mechanics of the Dark Web, and detail why it poses such a significant and evolving threat to contemporary cybersecurity strategies.
1. The Three Layers of the Internet: Surface, Deep, and Dark Web
To comprehensively understand the internet’s architecture, it is typically categorized into three distinct layers:
A. The Surface Web: The Visible World
- Definition: This is the portion of the internet that is indexed by commercial search engines like Google, Bing, or Yahoo, and can be accessed using any standard web browser (Chrome, Firefox, Edge).
- Examples: News sites, public blogs, social media profiles, and general e-commerce pages.
- Characteristic: It is the smallest and most visible segment of the entire web.
B. The Deep Web: The Unseen, but Legitimate World
- Definition: This vast section of the internet is not indexed by standard search engines. Search engine crawlers either cannot find these pages, or they are intentionally disallowed from indexing them. Accessing this content typically requires a login, password, or a specific direct link.
- Why it’s “Deep”: These pages are often created dynamically in response to a database query (e.g., searching a library catalogue), or their access is deliberately secured.
- Crucial Point: The overwhelming majority of content on the Deep Web is entirely legitimate and harmless. It exists primarily for privacy and security.
- Examples:
- Your personal email inbox (Gmail, Outlook).
- Online banking and financial account portals.
- Medical records and proprietary hospital databases.
- Subscription-based academic journals or streaming services.
- Company internal intranets and employee portals.
C. The Dark Web: The Concealed and Criminal World
- Definition: The Dark Web is a small subset of the Deep Web that has been deliberately hidden. It requires specialized software like Tor (The Onion Router) to be accessed.
- Characteristics: It is designed specifically for anonymity and uses non-conventional domain endings, such as the famous
.oniondomains, instead of.comor.org. - Purpose: While originally created for legitimate anonymous communication (military and journalism purposes), it is now predominantly used for illegal activities, hacker forums, and the trade of illicit goods and services.
2. Deep Web vs. Dark Web: The Critical Distinction
Understanding the precise difference between the two terms is essential for accurate risk assessment:
| Feature | Deep Web | Dark Web |
| Size | Constitutes approximately 90% of the entire internet. | A very small fraction of the Deep Web (estimated at <0.01%). |
| Indexing | Not indexed by search engines, but not intentionally hidden. | Intentionally hidden from search engines. |
| Accessibility | Accessible via standard browsers, but requires login credentials or a paywall. | Requires a specialized browser like Tor or I2P for access. |
| Purpose | Primarily legitimate and used for privacy (e.g., banking, personal data). | Designed for anonymity and often used for illegal or illicit activities. |
| Domain Name | Conventional domains like .com, .org, .gov, or .edu. | Exclusive .onion domains. |
Key Takeaway: All of the Dark Web is part of the Deep Web, but not all of the Deep Web is the Dark Web. Your banking information resides on the Deep Web; it is not, by default, on the Dark Web.
3. How the Dark Web Operates: The Role of Tor
The functionality and existence of the Dark Web are entirely reliant on the Tor (The Onion Router) network, which ensures user and host anonymity.
Onion Routing and Anonymity
- Layered Encryption: When a user wishes to access a Dark Web site, their request is wrapped in multiple layers of encryption, much like the layers of an onion (hence the
.oniondomain). - Circuitous Route: This request is not sent directly to the server. Instead, it travels randomly through a circuit of multiple volunteer-run Tor nodes or relays across the globe. Each node only unwraps one layer of encryption, revealing only the address of the immediately subsequent node.
- Impossibility of Tracing: By the time the request reaches the final server, the sender’s original IP address is completely obscured. The destination server cannot know the user’s true location, and the user cannot know the server’s true location, making tracing nearly impossible.
Cryptocurrency for Transactions
Transactions on the Dark Web are almost exclusively conducted using Cryptocurrencies, such as Bitcoin and Monero. Their decentralized and pseudonymous nature makes them the preferred method for criminals seeking to evade financial tracking and regulatory oversight.
4. What Happens on the Dark Web? The Hub of Cyber Risk
The Dark Web functions as a huge marketplace for cybercrime (Darknet Markets). Nearly every cyber security risk an organization or individual faces today can be sourced back to activity on the Dark Web.
A. Trading Stolen and Leaked Data
- Stolen Credentials: Hacked email addresses, login passwords, online banking credentials, and corporate network access keys are routinely sold in bulk.
- Personally Identifiable Information (PII): Large data dumps containing PII (names, addresses, birth dates, social security numbers) are packaged and sold to identity thieves.
- Financial Information: Stolen credit card numbers and cloned card data are highly sought after commodities.
B. Malware and Hacking Tools as a Service
- Ransomware-as-a-Service (RaaS): Complete ransomware kits, including the payload, command-and-control infrastructure, and technical support, are sold on a subscription or revenue-sharing basis.
- Exploits and Vulnerabilities: Information regarding new or Zero-Day Vulnerabilities in widely used software is traded confidentially at high prices.
- Hacking Services: Hired hackers offer services to conduct targeted attacks, DDoS campaigns, or corporate espionage against specific companies.
C. Other Illicit Activities
- Trafficking of illegal drugs, weapons, and restricted materials.
- Selling counterfeit documents, including passports, driver’s licenses, and government IDs.
- Trading in stolen intellectual property and insider corporate data.
5. The Direct Cyber Security Implications of the Dark Web
The existence and continuous activity of the Dark Web directly impact an organization’s security posture and risk profile.
1. Threat Intelligence and Monitoring
- Risk: If your organization’s data (e.g., employee email addresses, domain credentials) appears for sale on a Dark Web market, it signifies a high probability that an organizational breach has already occurred or is imminent.
- Defense: Security teams must employ Dark Web Monitoring tools and specialized services. These tools actively search for references to their brand name, corporate email domains, exposed IP addresses, and employee credentials on hidden forums and marketplaces.
2. Phishing and Social Engineering Risks
- Risk: The combination of leaked emails and passwords available on the Dark Web fuels highly successful Credential Stuffing attacks and allows criminals to craft more credible and convincing Phishing emails.
- Defense: Mandatory implementation of Multi-Factor Authentication (MFA) across all accounts, regular password rotation, and continuous employee security awareness training are crucial countermeasures.
3. Corporate Data Leakage and Espionage
- Risk: Confidential competitive information, intellectual property, or critical internal business plans can be exfiltrated by insiders or external hackers and sold on the Dark Web, leading to massive financial and reputational damage.
- Defense: Deploying Data Loss Prevention (DLP) solutions and strict Privileged Access Management (PAM) helps control and monitor sensitive data to prevent its unauthorized exit from the network.
6. Is Accessing the Dark Web Risky or Illegal?
In most countries, using the Tor browser itself is not illegal, as it was developed for legitimate purposes like enabling anonymous communication for journalists, human rights activists, and whistleblowers.
However, accessing the Dark Web with the intent to engage in, or purchase, illegal materials or services is strictly prohibited and a punishable offense.
Inherent Risks of Accessing:
- Malware Infection: Many Dark Web sites are scams or designed to host malware. Curiosity can lead to downloading malicious files, keyloggers, or ransomware onto your system.
- Identity Exposure: While Tor provides anonymity, misconfiguration or specific attacks can still expose your real IP address or device information.
- Legal Scrutiny: Entering sites associated with serious illegal activity can potentially draw the attention of law enforcement agencies.
Conclusion: Awareness of the Shadow World
The Deep Web, which makes up over 90% of the internet, is primarily an essential space for preserving online privacy and housing vast amounts of private data. However, its small subset, the Dark Web, is a highly organized and active domain for cybercrime.
For effective cyber security and risk management, the Dark Web must be viewed as a critical threat indicator. While curiosity about the Dark Web is natural, attempting to access it without the necessary expertise and layers of protection is extremely risky. Understanding the hidden risks it presents and building commensurate defenses is now a non-negotiable requirement for a secure digital future.